
Communication Technologies for M-Payment
Mobile payments appeared in 1997, when the Finnish telecom operator Sonera allowed its
customers to pay for soda in vending machines using their phones through a bank account. Since
that time, the scope of M-Payment has significantly expanded, and nowadays, there are many
more solutions. Let’s find out how they work.
The number of mobile subscriptions around the world is growing. Special attention is now
being paid to the development of solutions for mobile payments. The situation is complicated
by the fact that service providers often focus on direct debit payments and credit cards. At the
same time, there are more mobile phone owners than bank account holders around the world.
This leads to circumstances in which an increasing number of payment service providers are
working together with mobile operators to enable their customers to pay in a way that is
convenient for them.
So, let’s look at the technologies and methods available for conducting mobile payments.
Mobile payments, or M-payments, are a form of payment in which a mobile phone,
smartphone, or any other wireless device must safely complete at least one stage of a
financial transaction via a mobile network or other wireless technology.
In order to make mobile payments possible, some technologies and protocols are needed.
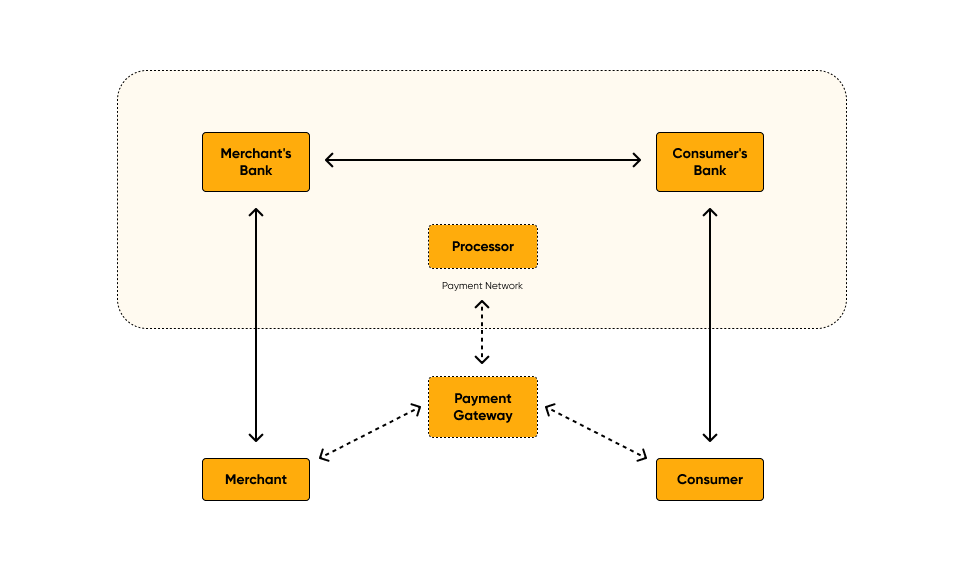
Basic minimum
- To make a mobile payment, you need several elements. In the simplest scheme, four elements
are enough: - Merchant (payee) — the one who sells goods and services, money is credited to his
account. - Consumer (payer) — the one who buys goods and services, money is debited from
his/her account. - Bank of the merchant — an institution that provides an account where funds are
received. Typically, it is a commercial bank, but not necessarily. - Bank of the consumer — an institution that provides a credit or debit account to a
consumer.
Alternative models include intermediaries, and then financial transactions are not made
directly: - Payment processor — a structure that coordinates and processes transactions between
banks or other financial institutions. Together with the seller’s and consumer’s banks,
they form a payment network. - Gateway — the link between the seller, the consumer, and the payment network.
Sometimes, these two elements can be represented as a single system.
Communication technologies for mobile payments
Using a mobile device, you can pay for purchases both near your location and at a distance. It
all depends on communication technology.
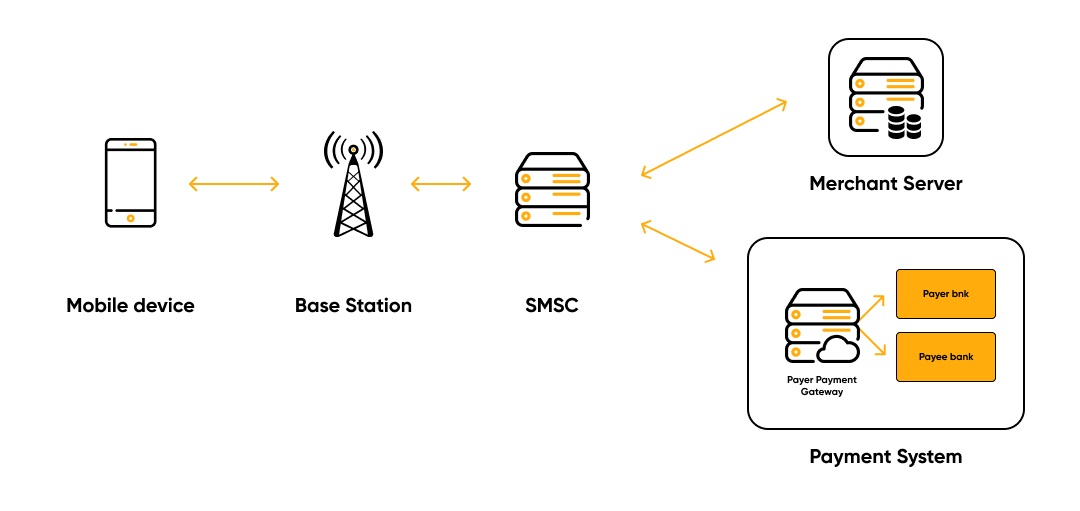
The Short Message Service (SMS) is a protocol that allows you to exchange messages of up
to 160 characters between mobile phones and an SMS center using GSM.
SMS payments include messages sent from or to a mobile device. That means that the cost of
the service is debited from the buyer’s account at the time of sending an SMS message to a
short number or at the time of receipt. If it happens at the time of receipt, the person sends an
SMS to a short number. If there is enough money in his account and the seller is ready to
provide the service, the customer receives a message for which a fee is charged.
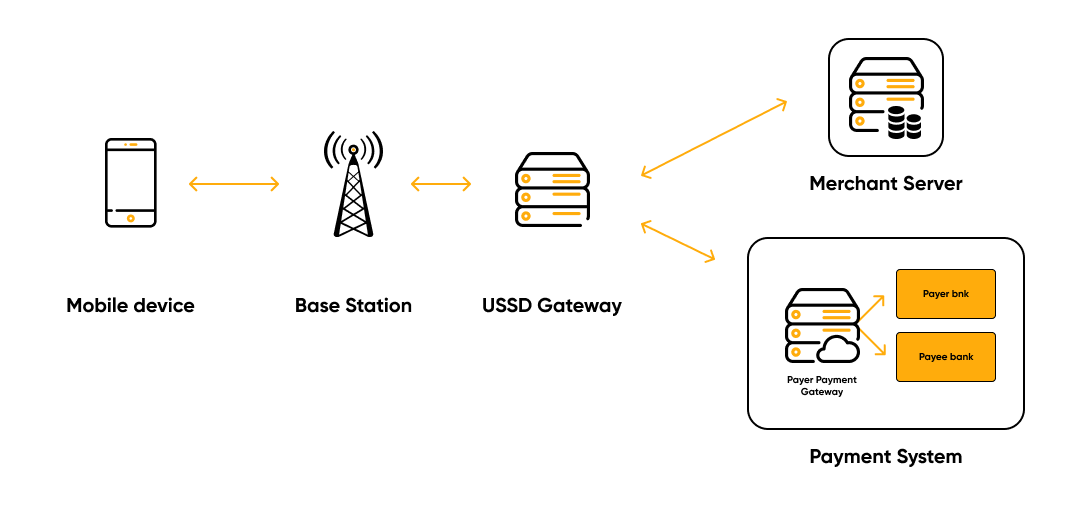
Unstructured Supplementary Service Data (USSD) is another protocol on GSM networks,
which, unlike SMS, has a direct connection between a mobile device and an information
application.
The buyer sends a USSD request to the seller. The command gets into the network and is
forwarded to the USSD gateway, which exchanges data over the SS7 protocol. When it
receives a request, it creates a session and sends it to the seller’s server or to the payment
system. To confirm the transaction, the response is received in XML format.
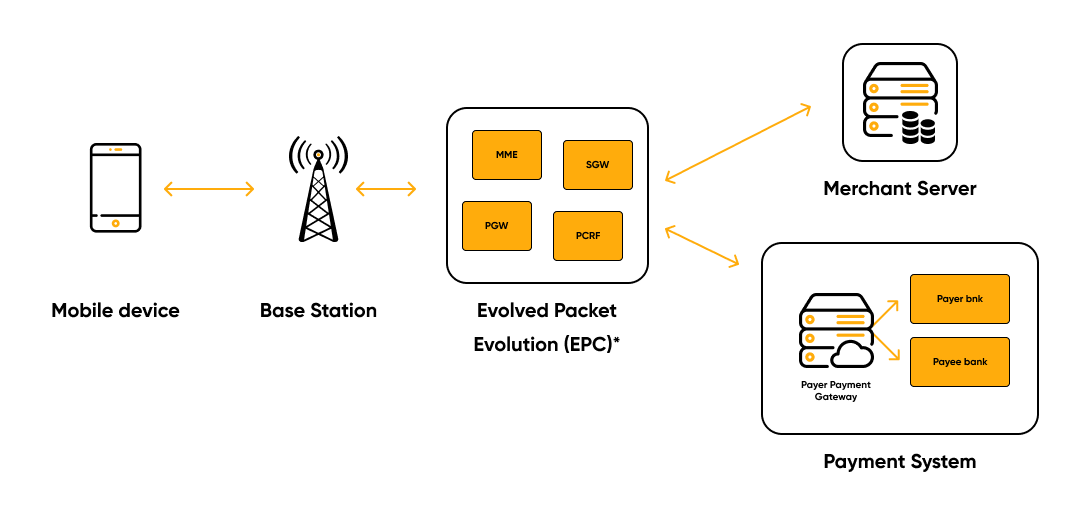
Mobile broadband access. The buyer sends a request via the LTE network, which goes to
the trading server. The transaction is completed by a payment gateway with the participation
of banks of both parties. The problem is that the operator acts as an Internet Service Provider
(ISP), although it should not interfere with the transmitted data.
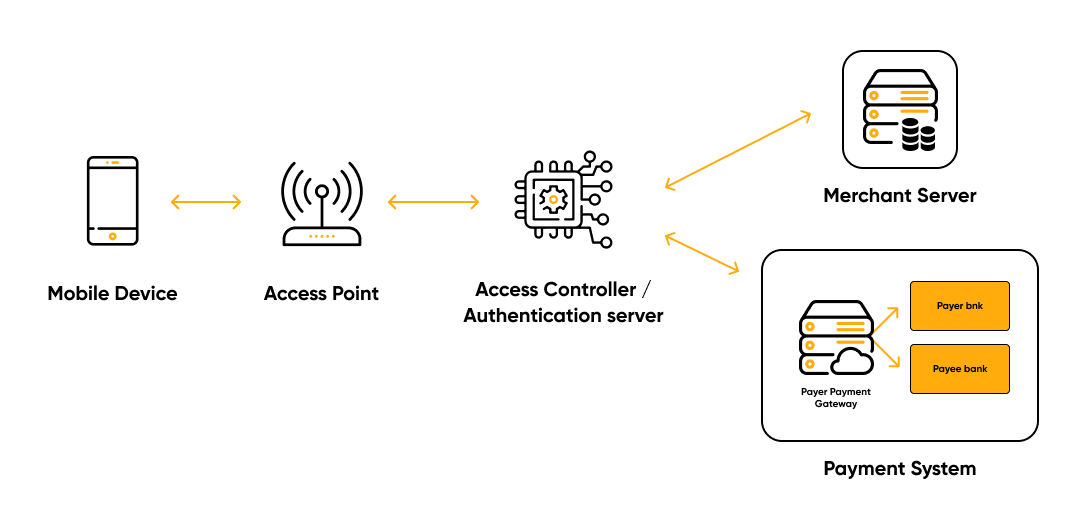
Wireless Local Area Network (WLAN) is an alternative to mobile broadband access is
wireless local area networks, primarily Wi-Fi. Devices that support WLAN are connected to
the Internet through them and can make transactions with retail outlets and banking servers.
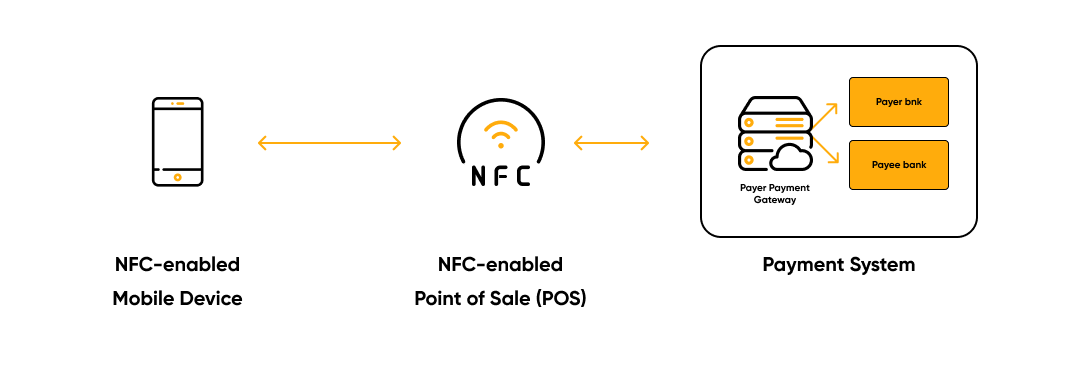
Near Field Communication (NFC) is a short-range wireless technology — just a few
centimeters. There are three main areas for applying NFC:
- Reading mode. NFC-enabled mobile phones can read NFC tags.
- Card emulator. The NFC device works like a contactless card.
- P2P mode. Two NFC-enabled devices communicate and exchange data.
In comparison with a WLAN, NFC technology has a «security element» (SE). It is a special
place in memory where confidential information is stored for verified applications.
Software platforms
The next generation of payments is connected directly to the mobile device, which means that
the client is using the payment system in an application format. The following types can be
distinguished.
Mobile application. There are different requirements for different types of operating
systems. For example, Android applications are developed in Java for GSM smartphones or
on the BREW platform for CDMA devices. For iOS, it is Objective-C.
An application based on a SIM card. The SIM Application Toolkit makes it possible for
the SIM card to be used not only for identification and authentication of a mobile device, but
also as a platform for applications. In return, it can store data more securely using
cryptographic algorithms.
Mobile wallet. An electronic wallet in the form of an application on the smartphone has
detailed information about the user’s bank account or card and allows him to pay for
purchases. The most famous mobile wallets are Google Wallet and Apple Pay.
Web applications. Sellers can create applications for browsers. Such a mobile client usually
consists of code written in JavaScript, CSS, HTML and a framework.
Payment methods
There are three main payment methods according to the connection options and the type of
payment.
- Direct billing. In this case, banks, mobile operators, and sometimes phone
manufacturers are involved. Upon purchase, the required amount is debited from the
client’s bank account and credited to the seller’s account. - Credit cards. The card number is linked to the customer’s phone number. When he
makes a purchase, the payment is withdrawn from the card and the money is credited
to the seller’s account. - Direct billing from the telecom operator. The purchase amount is paid on the
mobile phone bill. The operator identifies the buyer by SIM, so in this case, no
additional registration or login is needed. So, the purchase takes place in one click.
What are the security requirements?
The success of a particular payment method depends on how secure it is. In the case of
mobile payments, there are several minimum security requirements.
✔️ Identification. In the mobile payment system, identifiers can be a mobile phone number,
a user ID, or an account number.
✔️ Authentication. You can confirm the user’s identity using a token, SIM card, password,
PIN, fingerprint, Face ID, voice, and so on.
✔️ Authorization. Access rights for each party participating in the transaction.
✔️ Integrity. End-to-end data integrity is needed to ensure the accuracy of transaction
information in the messages between the seller and the buyer.
✔️ Privacy. In order for the payment system to remain secure, information about the trading
parties must be confidential. This can be archived when one of several cryptographic
algorithms is used.
✔️ Audit mechanisms and rejection of authorship. Here we are talking about transaction
logs, which store information about unique identifiers, timestamps, traders, and the cost of
services.
Obviously, there are no universal solutions for meeting these requirements. However, there
are some standards. To protect consumers, public and private organizations create rules for
financial transactions. For instance, the PCI Data Security Standard (PCI DSS).
How the largest payment systems work
Let’s look at how security protocols for mobile payments work, using the example of the
Stripe payment system.
This American company, which develops solutions for receiving and processing electronic
payments, offers sellers an impressive set of tools for securely collecting mobile payments.
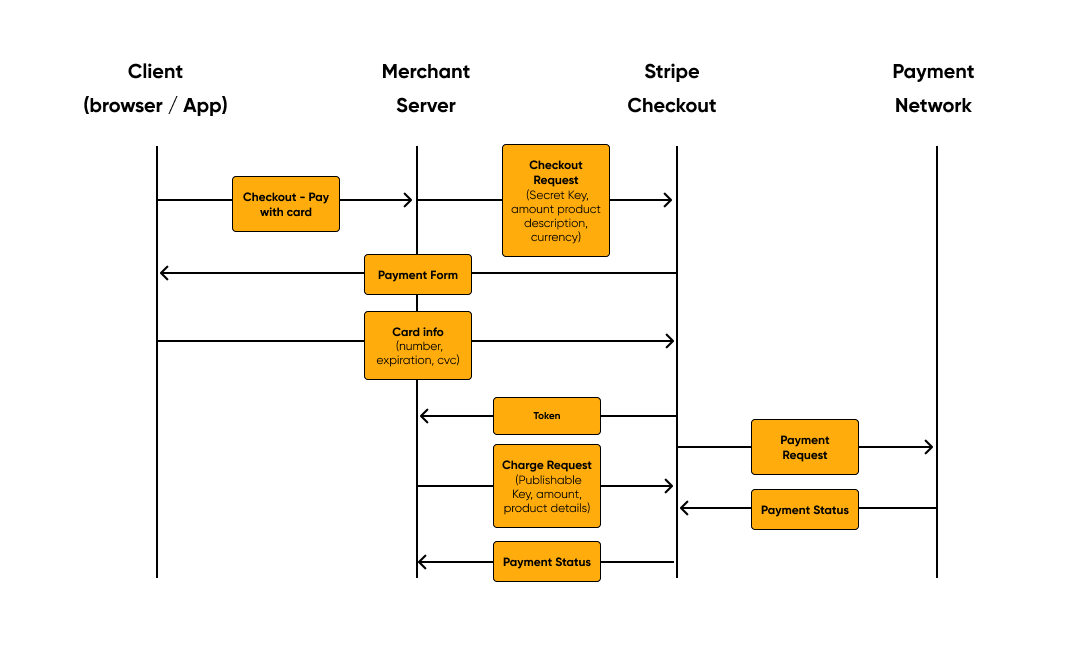
- Authentication. Stripe can only be used by registered sellers who have two keys: the
first for identification and the second a secret key for transactions. - Authorization. Stripe accepts requests only with a valid publishable API key. The
payment request is processed when the seller sends a valid secret key. - Confidentiality. The data that passes through the Stripe servers is encrypted using
secure HTTPS connections. The consumer can receive confidential information only
once, and the data is tokenized. - Compliance. When the seller integrates the order form, he undertakes to comply with
regulatory requirements, for example, PCI. Instead of processing the information
directly, it passes the responsibility to Stripe. The information is also stored in the
transaction logs, so it can be used for auditing in the future. - Integrity. Stripe uses tokenization and secure channels to transmit payment
information, thus preventing unauthorized changes in the transaction process.
Conclusion
We got familiar with various technologies, methods, and security requirements for mobile
payments, and also considered the protocol for completing transactions on the example of the
Stripe payment system.







 Searching...
Searching...